You are here
- Home
- Access and Identity Management (AIM)
- Groups
- Internet Society workshop on interfederation
Group administrators:
Internet Society workshop on interfederation
I’ve just had an interesting few days at an Internet Society workshop on interfederation: https://tid.isoc.org/confluence/display/interfed. Formal notes will be published soon, but here are some initial notes and thoughts.
The aim of the workshop was to identify the issues related to cross sector interfederation and determine actions that will help address them.
A lot of the discussion centred on liability and business models and levels of assurance –who pays if something goes wrong?; who pays full stop?; what’s the financial benefit of (inter)federation (the costs and benefits rarely apply to the same people)?
And the elephant in the room: 'Normal' people don't have identities, they have accounts, and accounts have contexts – an education context, a government context, a health context… so will citizens really want to use their same ‘account’ to be able to access everything?
Some practical suggestions included finding out from Service Providers whether they actually need proof of identity for their service or whether they actually just need credential management. Credential management is just knowing it’s the same dog rather than knowing it is ‘Snowy the white wire fox terrier’.
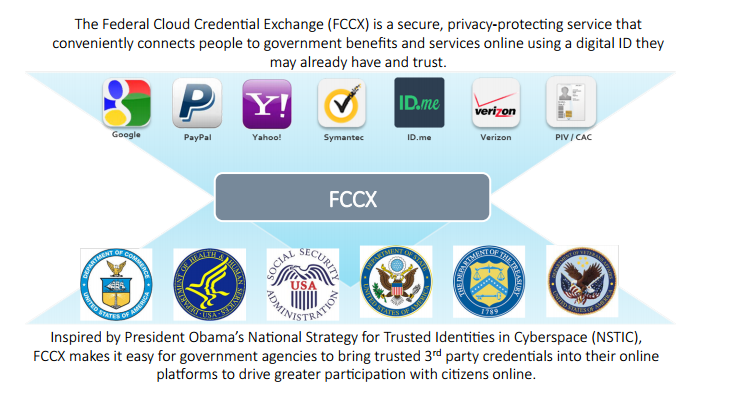
The US and UK government approaches are fairly similar with multiple IdPs connecting to a centrally managed hub that has a double blind architecture to prevent tracking of credential use among IdPs and SPs (so long as you trust the hub). One fairly major difference between them, though, is the IdPs that have so far signed up. The US Federal Cloud Credential Exchange (FCCX), which is soon to be rebranded connect.gov, includes Google and Yahoo! as IdPs. UK user testing has shown consumers don't want to use social logins for government services - social fits in well as a proof of living, but currently is unlikely to be used as an identifier.
Trust was also a common theme. A user needs to be able to trust that their data is safe. EU member states need to be comfortable in the trust of a German authenticating in Germany and using a service in France, for example. You can achieve this trust by explaining how things are built and used - setting base line standards so people know it is good enough. It doesn't have to be perfect. Standards for interoperability and security will help build trust, they also help us demonstrate to users and RPs that there is integrity and trust.
However, EU Regulation is not clear on where liability lies – it leaves it up to member states. For government interfederation there will need to be clearer decisions on liability otherwise costs will increase to compensate and functionality may be restricted for users.
An interesting proposal was made for privacy data leakage insurance – a model where if you hold personal data you need privacy insurance and the more data you hold the higher the premium you have to pay, however, this could be reduced by having good Identity Management in place.
One of the actions that will hopefully make it out of this meeting is some work on Levels of Assurance to move away from the traditional linear scale into something more useful and comparable that better fits an SPs actual needs rather than what they think they need.
On the topic of levels of assurance there was a good quote that "People say they want LoA, but do what they need to do to get stuff done." Sometimes the pragmatic solution is a more insecure method than federation without a stated “LoA”, but for others comparability could be acceptable: "I know this institution is doing the best for their needs and if it is good enough for them then it should be good enough for me."
Exchanging ideas and plans with other sectors is something we have been doing for a few years now and we have regularly exchanged ideas with various parts of the UK Government, but getting a wider experience has been very useful. Up until now it has been mainly an information exchange process, but given the global push – evidenced by attendance from identity people from the UK, US, NZ and Dutch governments and their involvement with European eID work, the time may almost be upon us to look at practical steps for interfederation between R & E federations and Government federations.
So, if anyone has a use case that requires interfederation between government and the UK federation, I’d be most interested in having a chat.






Comments
Re. "knowing it's the same dog": Andrew Cormack has pointed me towards a presentation he gave on this topic at the Nordunet conference: http://www.nordu.net/conference2009/ndn2009web/andrew_cormack.html