You are here
- Home
- Access and Identity Management (AIM)
- Groups
- Mobiles, Money and Millennials
Group administrators:
Mobiles, Money and Millennials
Last Tuesday’s OIX meeting covered an eclectic mix of identity assurance related presentations. Slides from all presenters should now be available on the shiny new http://oixuk.org/ website.
Steven Gevers from Verizon spoke on the “role of mobile in digital identity”. Describing the result from a recent Alpha project where Verizon explored the role that ‘mobile devices, SIM cards, networks and the subscriber data attributes that are unique to MNOs could play in the emerging digital identity ecosystem’. The idea of using heuristic data for identity assurance (given that most mobiles are always on, always connected and nearly always nearby) mean there are ways of telling whether the device is still in your possession or whether someone else is using it. This is further enhance by the ability to do dynamic challenge/response e.g. “how much was your last mobile phone bill?” The trial also used the SIM card to provide higher assurance by replacing a username and password with the mobile phone number of the individual (entered on the PC), and having the user enter a single, secret PIN on their mobile.
Next was an update from the Economics of Identity conference that happened last month. As I Tweeted when the related Whitepaper (http://oixuk.org/wp-content/uploads/2014/05/Economics-of-Identity-White-Paper.pdf) was announced, it backs up the last 10 years + of what we have been doing with federated access management:
The paper reported that more than 18 million identities are created each year (marriage certificates, birth certificates, mortgage applications etc.) at an estimated cost of £30 each. By adopting and reusing federated identities this cost can plummet by more than 80% for creating and 90% for reusing identities.
Another Whitepaper that has recently been published (http://oixuk.org/wp-content/uploads/2014/05/Investigating-the-Challenges-in-Digital-Identity2.pdf) is a report looking at Digital Identity Inclusion and Uptake in South Yorkshire. Working with a specific group of individuals chosen on the basis they were assumed to have a low-level of identity footprint (no passport, driving licence or other commonly held identity information available), this Alpha project involved a local Credit Union, a housing association and a GP surgery.
Interesting findings included:
- Online identity is badly managed and a security concern – most used the same password for all websites
- Habit and frequency affect identity in practice - public services online do not have the same frequency of use as retail sites so login details, processes or passwords were generally forgotten.
- Sharing is commonplace – many users in this demographic share identity information including Credit Union identities, Facebook and Twitter profiles.
- Mobile and email are a weak anchor to identity - Email accounts and sims / phones were frequently changed, forgotten, shared, lost or traded.
- Identity is about ‘now’ – the concept of building up a good credit rating is alien, so creating a new account isn’t a big deal.
Despite these issues the project found that an average of 24% of respondents could attain the levels of identity verification and assurance required to transact with most government services (GPG45 Level of Assurance 2). Also, using a federated identity saw a 10-20% improvement in the uptake of digital transactions compared with the current process of multiple user names and passwords to access online services.
Next up was David Rennie who provided an update on the Identity Assurance Programme:
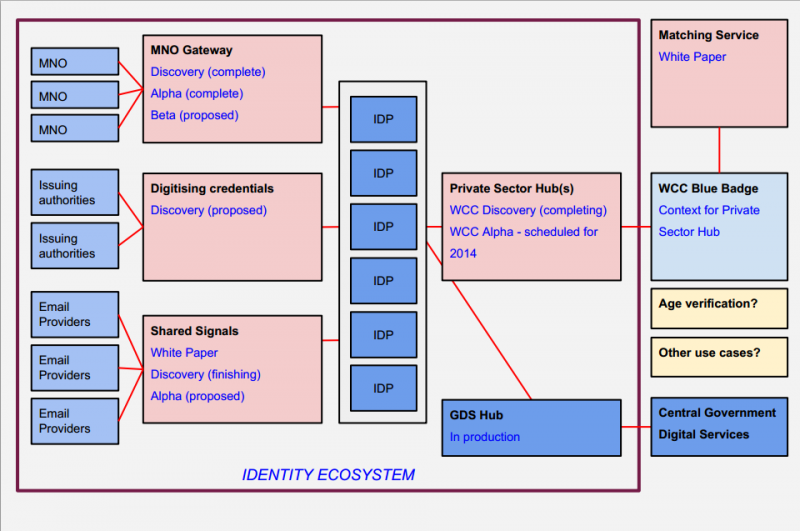
- MNO Gateway Verizon project. Means any IdPs can allow their users to use their mobile data and phone as part of the verification service. Discovery and Alpha complete and hoping to move into a Beta.
- Digitising credentials (Discovery proposed). Discovery is largely a paper based project that if looks promising becomes an Alpha.
- Shared signals White paper. Discovery finishing and Alpha proposed. This work describes a new collaborative system to share intelligence in an effort to protect the identity ecosystem by reducing the impact of fraud and account theft. Started with looking at email addresses. When an account is compromised it is obvious to lots of people as they get spammed by it, but there is no incentive to recipients to do anything about it. How can shared signals be used to alert the people affected? Could look at negative and positive signals. What happens if I register with one IdP but someone steals my identity and registers with another IdP?
- Private sector hubs / Warwickshire County Council hub Alpha scheduled for later this year.
- GDS hub in production (private Beta).
- Procurement 2 starting in September. Likely to be another market engagement day.
The July meeting concluded with some quick showcases:
- STORK: Robert Hann, Trustis
- Project STRIVE: Jon Shamah, EJ Consultants
- V-Auth’s Pin+, Virtual Two Step Authentication Solution: Steve Brittan
- Codel, Citizen Utility Bill Authentication, CUBA: Mike Jacobs
- ComSign Trust, PKI Solutions: Amir Gil
V-Auth's Pin+ solution is another attempt to simplify authentication by remembering a pattern rather than a password. It was presented as being a novel solution protected by various patents, but was very similar to a product I first came across almost 10 years ago called GrIDsure (http://gridsure-security.co.uk/). Unfortunately GrIDsure went into liquidation in 2011 and their solution was bought by Cryptocard, which in 2012 was bought by SafeNet (http://www.safenet-inc.com/multi-factor-authentication/authenticators/gr...).

And finally, an interesting point mentioned by Jon Shamah is that PEW Research has found that Millennials (those 18 to 33 years old, born 1981–1996) are less trusting than Generation X and Baby Boomers – something that may impact on our services (http://www.pewsocialtrends.org/2014/03/07/millennials-in-adulthood/sdt-next-america-03-07-2014-0-05/).





