You are here
- Home
- Access and Identity Management (AIM)
- Groups
- #idday or ‘not London IIW’ unconference
Group administrators:
#idday or ‘not London IIW’ unconference
11th June 2012 saw the first meeting of what will hopefully become a regular event looking at identity, personal data and personal clouds (#idday). Organised by Tony Fish (@tonyfish) and facilitated by Kaliya Hamlin (@identitywoman) the unconference was like a smaller, London version of IIW http://www.internetidentityworkshop.com/. Attended by about 30-40 people there was a good mix of delegates from universities (Imperial, Cambridge, Reading and Goldsmiths), start-ups and large companies (including BT, Unisys, Ping Identity, Miicard), as well as about half of the Cabinet Office GDS team with @DavidRennie. It was nice to actually meet some of the people in the flesh who I have only previously spoken to; followed on Twitter; or read their work online - not least Dave Birch (@dgwbirch), John Bradley (@ve7jtb) and Drummond Reed (@drummondreed). The day was split into 5 different sessions each with multiple streams with the agenda set by the attendees at the start of the day. Notes from all the sessions are being collated by Kaliya and I’ll add a link to them when they are live. For now I’ll post my brief notes here.
Session 1 - User-centric IdM vs Insitution-centric IdM
I led a session looking at how to address the issue of interoperability between the traditional institution centric approaches to identity management with the user-centric approach gaining speed and promoted by most of the attendees. Although the attendees in my session didn’t come up with any definitive answers (not that I really expected them to) the discussion was very interesting and covered a range of topics: levels of assurance; data protection laws; the need to separate identity providers and attribute stores; the differences between managing access and managing identities; lack of a common vocabulary and shared understanding between organisations e.g. different interpretation of roles across different institutions.
With the increase in user-centric identity management (IdM) will there still be a need for institutions to manage identities? Yes, but not necessarily how they do so now. Universities can vouch for certain things, such as this person is a Physics student at the university so can access a particular journal, but students will have a growing series of attributes that could or should be asserted from different attribute stores. Some of which will need to be certified e.g. to prove that Joe Bloggs did get a BA in Maths and Politics from the University of Keele.
Providing access to resources is the easy bit. How do you prove the identity of a student to prevent fraud?
Identities or personas - most people have, or need, at least 4:
- Government
- Finance
- Employment
- Anonymous
We are moving towards federated trust.
Context and relevance is important.
A UK driving license is not an 'identity document'.
There are data protection issues of data sharing between government departments.
Users need a choice of what documents to use and when.
One delegate proposed a codified user agreement so that citizens could propose their own data sharing agreement to a company and an app will highlight conflicts between the company’s and the citizen’s so they can decide whether to shop there or go elsewhere.
A university is:
- an attribute provider
- a credential service provider
- a bulk purchaser of services
- a manager of subscriptions and relationships.
The problem of managing a lifetime of credentials: how do you maintain access as roles change? Universities may not want to be lifetime identity managers/attribute stores, but some will to maintain alumni relationships and for revenue.
With multiple identity providers and attribute stores, there is an issue of managing chains of trust. What is the attribute and what is the provenance?
Sometimes a personal data aggregator is a good thing, but sometimes business reasons mean there has to be central verified aggregation.
You build trust by establishing who is good.
Session 2 - GDS Alphas
Stephen Dunn from the Government Digital Service (GDS) outlined some of the Alpha projects they are involved in. The identity assurance (IdA) hub architecture is being developed and released as open source.
1. Voter registration - Basic Alpha created. Identity assurance (IdA) is needed to prevent fraud. Electoral roll Alpha will be first in the IdA ecosystem. It will forward data on to a local authority. This Alpha will feed into Ordnance Survey work to create a single register of addresses in a single gazetteer (http://www.geoplace.co.uk).
2. Working with the Office of the Public Guardian (www.justice.gov.uk/about/opg) an agency with responsibility for registration for Lasting Powers of Attorney. This Alpha will prevent OPG from having to manage lots of paper forms. Very simple account management to start with.
3. Anti fraud Alpha. A National Fraud Intelligence Bureau project to see how known damaged identities can feed into the ecosystem.
4. Universal credits in Sheffield. Working with a credit union and a single street to put in NFC readers to allow payments via smart cards. Transaction records become trust documents for those that don't have 'traditional' id.
5. Registration of a small business. Currently reported fraud of £73Bn a lot of which is related to small businesses. Easier to solve as privacy not an option and could be mandated by Government.
6. Age verification. Starting to talk to payments companies about scoping an Alpha.
Session 3 - Trust
A select gathering talking about Trust.
Trust tends to mean different things to different people. Members of the public see trust as allowing their data to be used for a specific purpose and that their data will be well managed. Business to business trust can be described more as a chain of assurances where each link asserts their policies are the same as the next.
Consumers don't trust banks, but do care that they won't lose out by providing data e.g. if a bank does something wrong then they get redress.
How do you trust devices? Internet of things.
Trust needs a context.
For Trust to work you need enforceable processes. A User needs to know someone will suffer if something goes wrong!
For a Trust Framework you need technology, policies, and enforcement.
Need metadata around policies.
Need layered policies.
Need policy wrappers with different LoA.
Need a standard for a policy framework.
Communities of trust - how do you mechanistically define trust?
Kantara has an Assurance Review Board that accredits assessors who can perform Kantara Service Assessments at various assurance levels. The Identity Assurance Framework enables relying parties to understand the trustworthiness of electronic identity credentials issued at commonly agreed levels of assurance.
Need a standard structure format and location for policies.
Session 4 - OpenID Connect
John Bradley provided an update on OpenID Connect - http://openid.net/connect/. OpenID Connect is basically OAuth plus identity from OpenID 2.0, but is a complete rewrite.
Not so many people are bloggers as OpenID developers initially thought...
Roland Hedberg has an OpenID Connect end point (see his TNC talk at https://tnc2012.terena.org/core/presentation/86).
OpenID Connect is following a similar model to IETF with cycles of implementations, aiming to go final at end of year. Ping very well developed. Tivoli looking at it. CA working. Paypal/ebay are opensourcing their implementation under the name Oreo Cookie.
OpenID Connect breaks apart credential service provider and attributes.
John mentioned a vulnerability he discovered in the way Facebook (and others) is using OAuth for authentication. He has blogged about it at http://www.thread-safe.com/2012/01/problem-with-oauth-for-authentication.html.
John also mentioned Trust Frameworks and how OIX can help set them up and certify assessors for that framework (http://openidentityexchange.org/how-it-works/what-is-a-trust-framework).
Session 5 - the Personal Data Ecosytem
Kaliya led a discussion on the personal data ecosystem, looking at various companies working in this area including Privo (http://www.privo.com/) a niche provider looking at children's data and parental responsibilities.
Different companies have different business models:
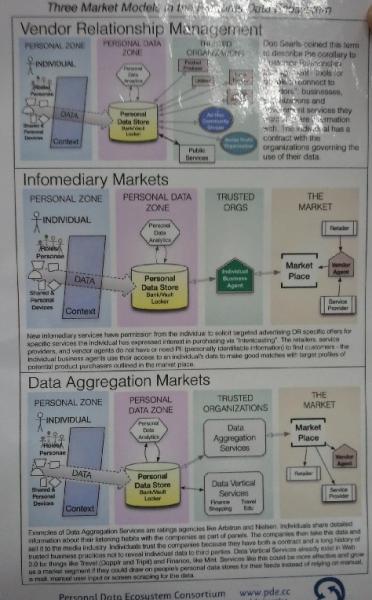
Many PDS are starting to come on board and there are many that make use of your data for your benefit in one particular vertical. Among the companies mentioned were:
- Mint - finance
- Smarchive - Smart archive
- Doo.net – digital documents
- Xobni - inbox backwards – for smarter inbox and contact management
- TripIt - travel
- Dropbox – storage
- Personal.com – store and share your personal information - has $12m in venture funding
- Qiy – ‘independent trust framework for guaranteed digital identities’ has received €10m in Government funding (Netherlands)
- Singly - an open personal data platform has $7m funding.
It will just take one travel company e.g. Expedia to hook up with a PDS company with a travel 'form' to invigorate the market
Bonus session - XDI
Drummond Reed had spent most of his flight over to London finishing a presentation on XDI (XRI data interchange) so it would have been rude not to stay and see it. And I am glad I did – it was fascinating. So much so that I didn’t take many notes, but the paper that it was based on by Drummond and Phil Windley will be shortly published at www.Kynetx.com so you can read all about it shortly.
Basically, XDI is a way of achieving interoperability for personal data stores allowing any-to-any data interchange. So a PDS doesn’t actually need to be a ‘store’ it can be just a server that brokers data.
Semantic XDI will facilitate ‘personal channels’. Again there is a paper coming out on this at http://respectnetwork.com/the-personal-channel/, but the concept is billed as a communication link that is “... as different from email (or text, or chat) as fax machines are from ordinary telephones.”
Personal channels will mean:
- No spam
- Never lose contacts
- Secure delivery
- Simple standardised contextual authentication
- Scalable trust with contextual reputation
- Automated event processing e.g. game change for a lacrosse team
- Intelligent filtering and organisation
- Intelligent notification
- Automatic data exchange
- Rich sharing
I’ll add a link to the slides when they become available.






Comments
Drummond and Phil's white paper on Personal Channels is now available at http://www.windley.com/pchan/