You are here
- Home
- Access and Identity Management (AIM)
- Groups
- Highlights from #TNC14
Group administrators:
Highlights from #TNC14
The Terena Network Conference #TNC14 was so interesting and busy that I didn't get time to drip feed the sessions as I advertised in my previous post, so instead, here is a selection of the AIM highlights. Most sessions were recorded so for more information you can view the archived streams at https://tnc2014.terena.org/web/media/archive/.
Simplifying Federation Deployment
https://tnc2014.terena.org/web/media/archive/2B
IdP in the cloud: identity management as a service at GARR
https://tnc2014.terena.org/core/presentation/31
An update from the Italian NREN (GARR) about their IdP in the Cloud work. This is a way to simplify the adoption of federated Identity solutions, particularly for smaller institutions. It is a virtual appliance consisting of the IdP and identity management tools. Currently hosts LDAP on behalf of sites, but if required could link to an existing AD or LDAP.
Think Globally, Act Locally: Simplifying Federated Technologies
https://tnc2014.terena.org/core/presentation/57
The Canadian and Swedish federations have collaborated on developing tools to increase the adoption of federated identities including an interactive configuration builder that simplifies setting up an IdP for eduroam and Shibboleth. See the demo at
http://youtu.be/7DpHL9akgrg
GÉANT TrustBroker: Dynamic inter-federation identity management
https://tnc2014.terena.org/core/presentation/17
To interfederate, IdPs and SPs need to join 1 or more federations. This isn't always desirable for large international groups as there can be complex contracts and lots of manual work. The goal of the GEANT Trustbroker project is to to connect IdPs independent of federation borders by dynamically establishing workflows, trust and configs - creating virtual federations.
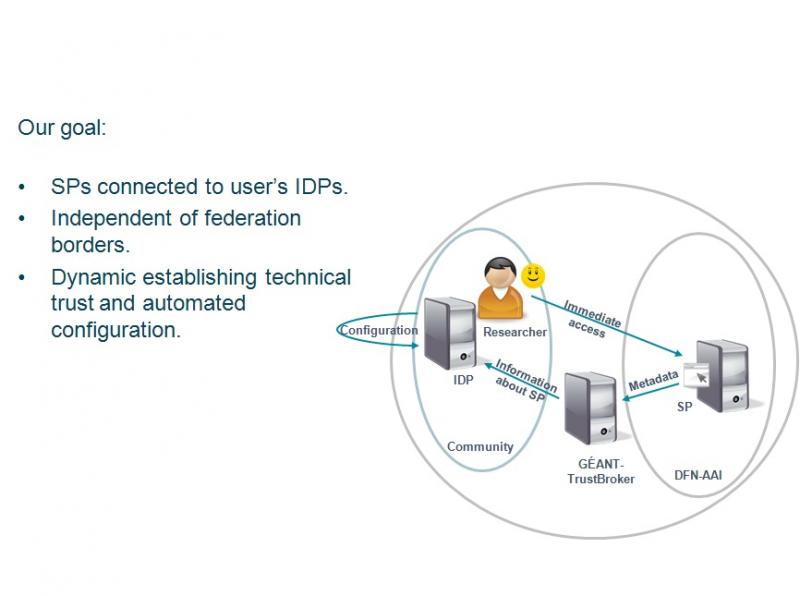
Federated identity in research and education
https://tnc2014.terena.org/web/media/archive/6C
Building the “Swiss edu-ID”: status and outlook
"Swiss edu-ID" is an attempt to provide a lifelong identity that puts users in control. SWITCH - the Swiss NREN - is the owner of the eduID scheme, but it is a user-centric identity system so the user will be in control. Benefits include a single identity for lifelong learning, longer term relationships with SPs, easier for libraries to track authors (possible link with ORCID). Will support, or be interoperable with, SAML (SWITCHaai); X.509 (SuisseID, STORK); Oauth2/OpenIDConnect (to link with external IDs - ORCID, social media ids, mobile device support, linking attribute authorities.)
An interesting idea, but as @sidejackable stated "surely a life long eduID is a pipe dream? It assumes the issuing body will "live"/"be interested" longer than the person." Lifelong identifiers may be more achievable, but still need funding/support forever. Also, what happens when you move across borders e.g. you teach in Germany and Switzerland? Do you get a Swissedu-ID and a Germanedu-ID? The answer given was that with interfederation you could use one in the other country. But there are obviously still a lot of questions on this whole area. One to watch.
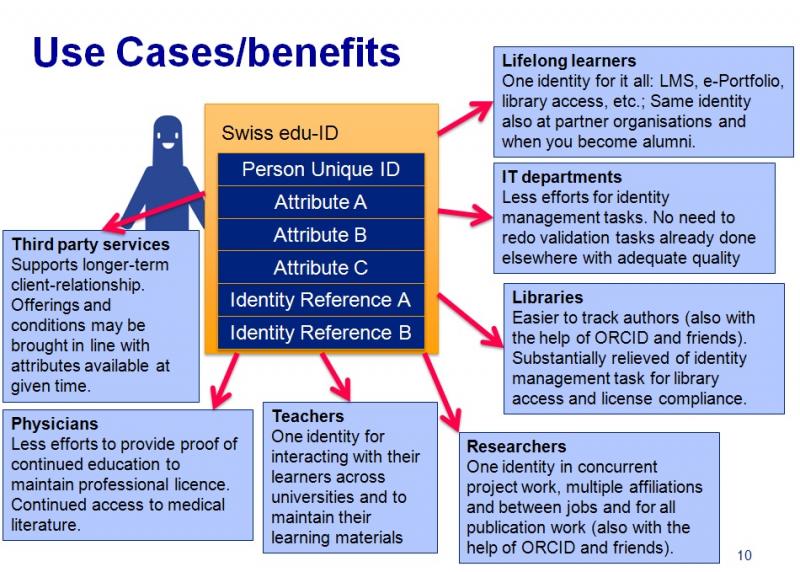
How eduGAIN can help education: a real life story
https://tnc2014.terena.org/core/presentation/59
This session was essentially an advert for eduGAIN - but you already know about eduGAIN, don't you? It is a way of getting access to services in other countries federations so IdPs and SPs don't have to join multiple federations. To participate in eduGAIN from the UK federation take a look at http://www.ukfederation.org.uk/content/Documents/EduGAINParticipation (in case you hadn't noticed, this website is available via eduGAIN).
Case Studies in Federated Identity Management for Research Communities
https://tnc2014.terena.org/core/presentation/64
In GN3plus, the AAI providers of eduGAIN and the scientific communities of FIM4R (Federated Identity Management for Research) have teamed up to deliver a series of pilots that address challenges for research communities in using Federated Identity. This presentation showed the work and progress of the pilots and outlined future developments. This is well worth a look at if you or your institution deals with any international research groups or projects (EUDAT, CLARIN DARIAH, WLCG, EGI, LIGO etc.)
Better safe than private
https://tnc2014.terena.org/web/media/archive/8B
The privacy paradoxes
https://tnc2014.terena.org/core/presentation/22
Ken Klingenstein kicked off these three presentations in his inimitable style looking at the conflict between end users and identity federation administrators around attribute release and access control.
I particularly liked the reference to Alan Westin's categorisation of end users and their attitudes to privacy: fundamentalists (generally distrustful of organisations that ask for their personal information); pragmatics (weigh up the benefits to them of consumer opportunities versus data sharing); unconcerned (generally trustful of organisations collecting their personal information). Ken looked at how we can nudge users to be more privacy aware and demoed PrivacyLens, an NSTIC funded open source privacy manager (https://github.com/cmu-cylab-privacylens/Privacy-Lens).
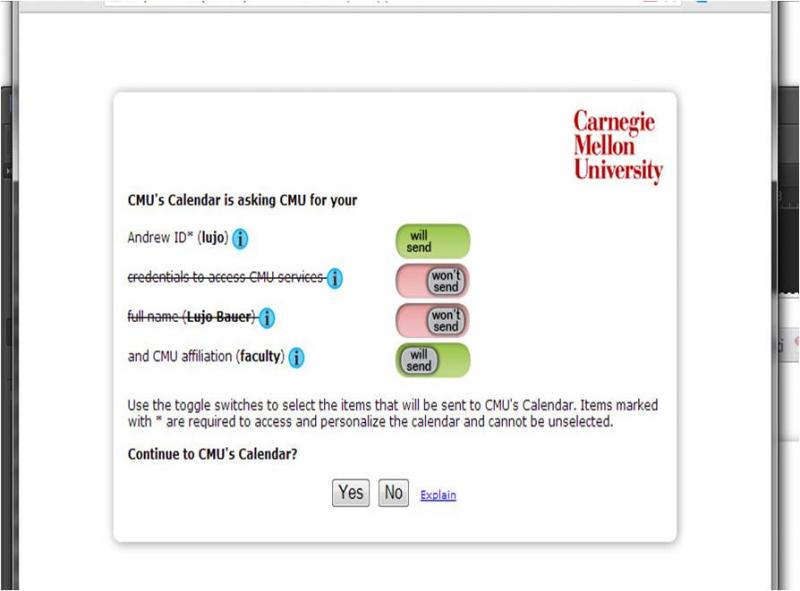
Group authorisation and licensing for federated cloud services
https://tnc2014.terena.org/core/presentation/43
There appear to be a number of group managers that can help with managing authorisation and I've been meaning to look at them in more detail. Perhaps I'll blog about them later this year. In the meantime Bob Hulsebosch's presentation looked at three high-level approaches to orchestrating authorisation for group-based licenses: SP-centric, IdP-centric and Group-centric.
Allowing the user to define the attribute release policy
https://tnc2014.terena.org/core/presentation/12
Finally, Roland Hedberg gave a technical overview of the User managed access (UMA) profile and extension to OAuth 2.0. I didn't take any notes in this session so from the abstract: UMA defines how resource owners can control protected-resource access by clients operated by arbitrary requesting parties, where the resources reside on any number of resource servers, and where a centralized authorization server governs access based on resource owner policy. Combining SAML2 and UMA might then be one way of allowing individuals to manage their attribute release. But the SAML2+UMA combination may also solve other problems like: having different entities managing different portions of the same dataset or letting an IdP gather information from several different datasets under the same or different policy regimes or having the users information in one central place and then allowing different identity providers access to user controlled views of the users information.





