Group administrators:
Recent members:
Calling Station Identity
Calling Station Identity Missing in Significant Proportion of Access-Requests Being Sent to the NRPS Dec 2014
CSI Recap
Inclusion of the Calling-Station-Identity attribute in Access-Requests generated by APs and WLCs (and switches, if wired eduroam is offered) is a mandatory requirement of the UK Technical Specification (and the European Service Definition for SPs). The CSI is used to uniquely identify the device the user is authenticating from and must include the MAC address of the device. The Tech Spec states it is essential that this attribute is logged at both SP and IdP sites. This ensures that participating organisations are able to comply with the Janet Security Policy. When matched with DHCP logs, a link between the user's device, an IP address and an authentication event can be definitively proved - essential in cases of investigation of network access abuse.
How well is the Community Complying with this Requirement?
All RADIUS traffic sent to and forwarded by the NRPS is logged, which facilitates both troubleshooting and usage monitoring. The NRPS logs enable a monthly count to be made of the total number of all Access-Request events and also the total number of Access-Request events not containing CSI. In order to reveal how successfully member organisations are complying with the Tech Spec in this regard, these two counts are compared. The chart below presents the results.
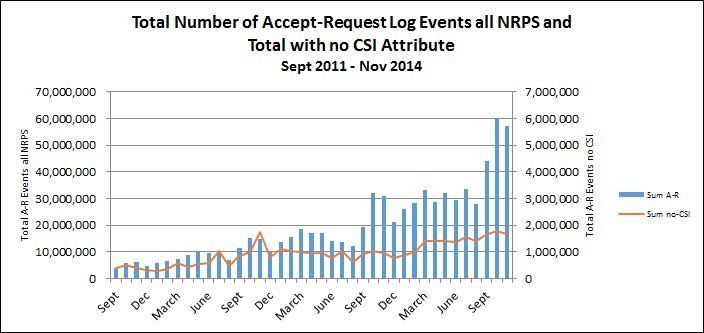
Note that the no-CSI events axis is 1/10 of the total A-R events count.
Why would there not be CSI in an A-R sent to the NRPS?
As far as is known, there are no 802.1X compliant NASs that are not capable of including CSI. The reasons for no CSI are a) misconfiguration of NAS b) misconfiguration of ORPS such that it filters out CSI from A-Rs forwarded to the NRPS c) use of AUTH command for status check of NRPS (as documented in the old Sussex FreeRADIUS case study) - the 'ping' status-check method should be used instead.
How can a Sys Admin check to see if ORPS is sending A-Rs with no CSI?
This should be pretty obvious from your ORPS logs!
Sys admins can also look in the 'Examine Problem Log Files' function on the Support server. This allows the sys admin to see daily excerpts from the NRPS logs filtered for their organisation and particular issues. Check the identifier and realm error files to see if CSI is present or blank.
Conclusion and Actions Arising
It is heartening to see that the proportion of A-R with no CSI has fallen over time. Nevertheless the proportion remains too high. A significant fraction (28%) of no-CSI A-R events arise from outside of the UK eduroam zone and as such we have no authority to require the organisations from which these originate to correct their services. However UK participants which are not including CSI are currently being requested to investigate and rectify such non-conformance.





